Cybersecurity Course Portfolio
Our Training Portfolio
In order to provide a better overview and to facilitate access to the course program you are looking for, we have organised our portfolio in two main domains:
- Technical Domain
- Core Domain
Our Technical domain portfolio includes courses related to:
Our Core domain portfolio includes 5 domains:
Technical Domain Portfolio
Applied Web Security
Web application security is a branch of information security that deals specifically with the security of websites, web applications and web services. At a high level, web application security draws on the principles of application security but applies them specifically to internet and web systems.
Web Application Security Intermediate - RT422
The Web Application security course will help participants understand major web application flaws and their exploitation, as well as learn a proven process for locating these flaws consistently.

Web Application Security Advanced - RT423
This training is an advanced course that covers topics in the Red-Team Cyber Warfare methodologies.

Industrial Control Systems
Intro to ICS/SCADA - BT222
The Intro to ICS/SCADA program was constructed primarily for the security industry and was meant to equip participants with understanding of the world of ICS.

ICS Forensics - BT223
The program was designed comprehensively and professionally, to impart the skills and knowledge required to integrate into key positions of the information security world, both in defense and attack teams.

IoT Exploitation - RT430
The course will be based on both theoretical and practical use of vulnerabilities in IoT devices, IoT devices architecture, identifying attack surfaces, and exploiting IoT vulnerabilities.

ICS Penetration Testing - RT431
This training covers possible attack methods by hostile entities and the security challenges that naturally follow.

Cybercrime investigation
Cryptography - BT216
From ancient examples of secret messages and the spies that cracked them to modern cryptographic applications, you will have the opportunity to explore the foundations of data security.

Reverse Engineering - BT221
This course sets the groundwork of understanding networks and the investigation process on them.

Core Domain Portfolio
Foundations
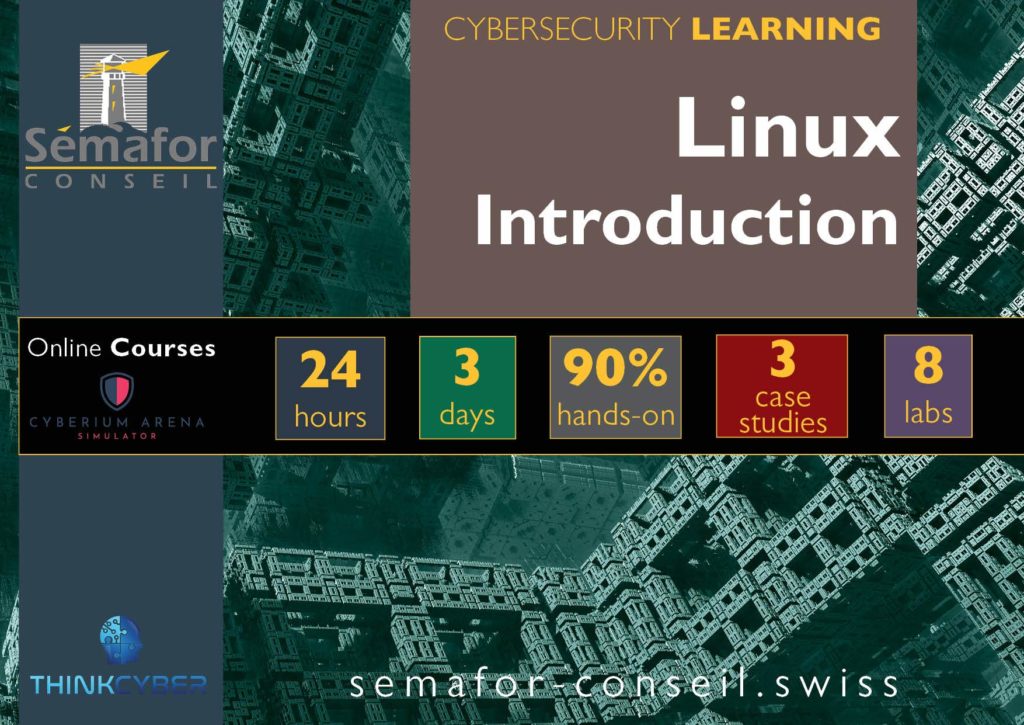
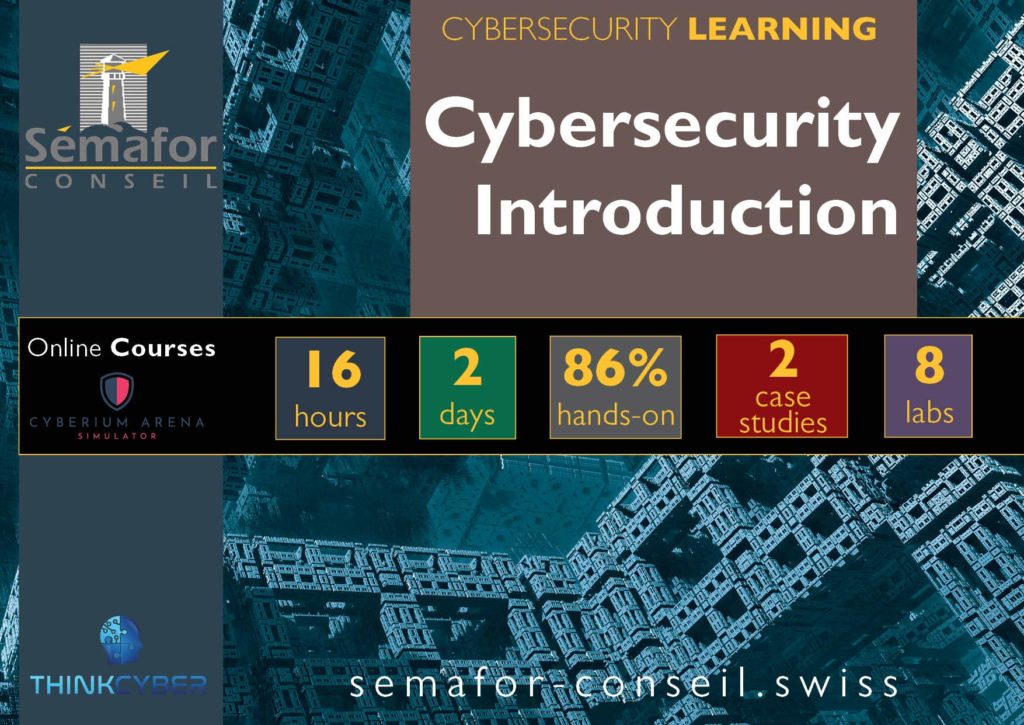
Cybersecurity Introduction - NS101
Cybersecurity Introduction training covers the core concepts of defense and understanding in the practical world using the CYBERIUM ARENA simulator. Students will learn about different domain structures and security technology products.
Warning: Trying to access array offset on false in /home/clients/0693dfda65b5b933cf10a4fc8f7a540d/sites/dev.semafor-conseil.ch/wp-content/plugins/exclusive-addons-for-elementor/elements/accordion/accordion.php on line 1290
Cybersecurity Advanced Notions - NS102
Cybersecurity Advanced Notions course is designed for experienced computer users who have limited or no previous exposure to Linux, whether they are working in an individual or corporate environment.

Security Advanced Notions - NS106
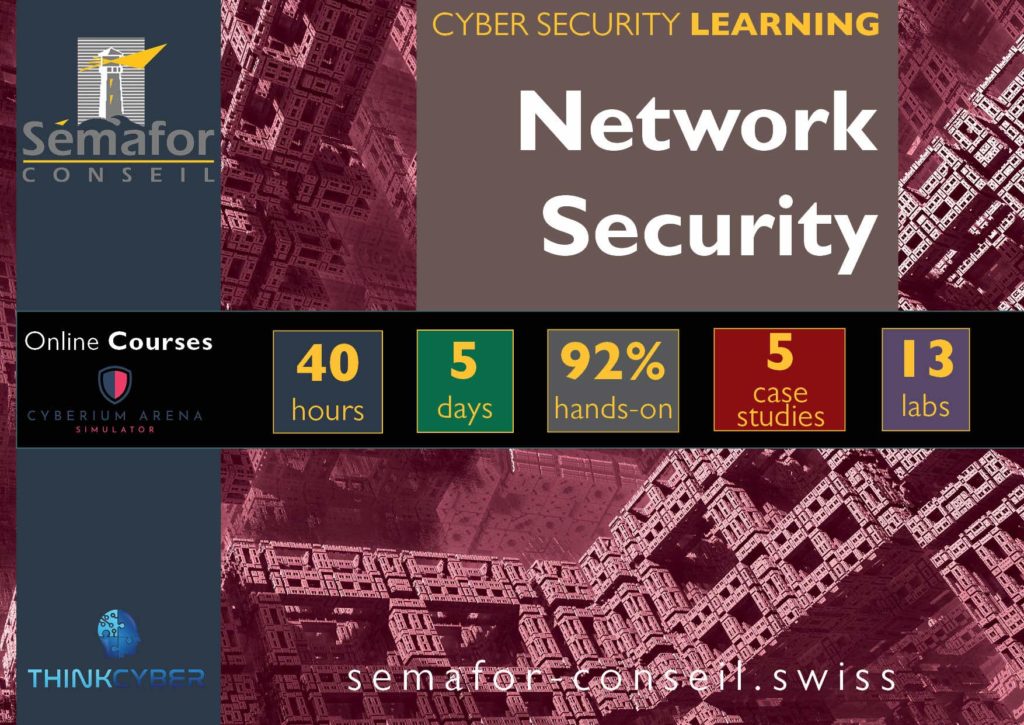
The Network Security course aims to address cyber challenges experienced on the network level. The course covers various attack techniques and how to defend against them.

Network Security - BT208
After this course, you will be able to discover security vulnerabilities across the entire network by using network hacking techniques and vulnerability scanning.

Cryptography - BT216
From ancient examples of secret messages and the spies that cracked them to modern cryptographic applications, you will have the opportunity to explore the foundations of data security.

Monitoring, Detection, Defense Operations
SIEM/SOC Intermediate - NS107
This course covers the necessary skills and practices to train such SOC personnel and successfully operate a modern-day SOC.

SIEM/SOC Advanced - NS108
This SOC Operation course is designed for SOC organizations implementing a SOC solution and provides full guidance on the necessary skills and procedures to operate it.

Threat Intelligence and OSINT - BT209
This course teaches participants how to collect and analyze information using various tools and unique methods and apply targeted cyber intelligence to defensive operations to act on threats proactively.

Penetration Testing Intermediate
Penetration Testing - BT212
This training will provide the participant with a steppingstone on how to use it in practice and take on the complex task of effectively measuring the entire attack surface of a traditionally secured environment.

Cyber Warfare - RT420
This training is an advanced course that covers topics in the Red-Team Cyber Warfare methodologies.

Offensive Python - RT421
The course offers participants advanced levels of attack to evade the many defense mechanisms available in the market today with the help of independent tools and Python programming capabilities.

Web Application Security Intermediate - RT422
The Web Application security course will help participants understand major web application flaws and their exploitation, as well as learn a proven process for locating these flaws consistently.

Exploit Development Intermediate- RT433
This course covers how to write shellcodes, programs, and tools, essential skills for advanced penetration testers and software security professionals.

Windows Exploitation - RT424
In this training, you will learn about the Windows operating system, and you will experience in both offensive and defensive methods, knowing how to break into the system is not the same as understanding how to defend against the attack.

Penetration Testing Advanced
Web Application Security Advanced - RT423
Testing web-application security is not intuitive, and to be useful, you need an understanding of web application design, HTTP, JavaScript, browser behavior, and potentially other technologies.

Exploit Development Advanced - RT434
This training is an advanced course that covers topics in the Red-Team Cyber Warfare methodologies.

IoT Exploitation - RT430
The course is based on both theoretical and practical use of vulnerabilities in IoT devices, IoT devices architecture, identifying attack surfaces, and exploiting IoT vulnerabilities.

Intro to ICS/SCADA - BT222
The Intro to ICS/SCADA program was constructed primarily for the security industry and was meant to equip participants with understanding the world of ICS.

ICS Penetration Testing - RT431
This training covers possible attack methods by hostile entities and the security challenges that naturally follow.

Incident Response, Threat Management Forensics
Windows Forensics - BT210
Windows Forensics is an essential skill in the cybersecurity world. This course covers a broad spectrum of aspects of the forensic investigation process performed on a Windows OS.

Network Forensics - BT211
This course sets the groundwork for understanding networks and the investigation process on them.

Linux Forensics - BT214
During this course, participants will learn the basics of computer hardware and the Linux-OS files system.

Python Forensics - BT215
This training will provide the participant with steppingstones on how to take forensics skills to the next level, combining them with powerful Python scripting.

Malware Analysis - BT220
This course provides participants with the practical skills and knowledge to be able to analyze malware and exposes them to a critical set of tools required for their tasks.

Reverse Engineering - BT221
Reverse Engineering is a technique used to analyze software to identify and understand its components and its flows. It is a process of understanding code infringement processes and analyzing software weaknesses.

ICS Forensics - BT223
The program was designed comprehensively and professionally, to impart the skills and knowledge required to integrate into key positions of the information security world, both in defense and attack teams.

Courses open for subscription
CyberLearning - Educational Process
This course explores the various tools and techniques commonly used by Linux system administrators and end-users to achieve their day-to-day work in a Linux environment using automation techniques. Linux Operations course is designed for experienced computer users who have limited or no previous exposure to Linux, whether they are working in an individual or Enterprise environment.
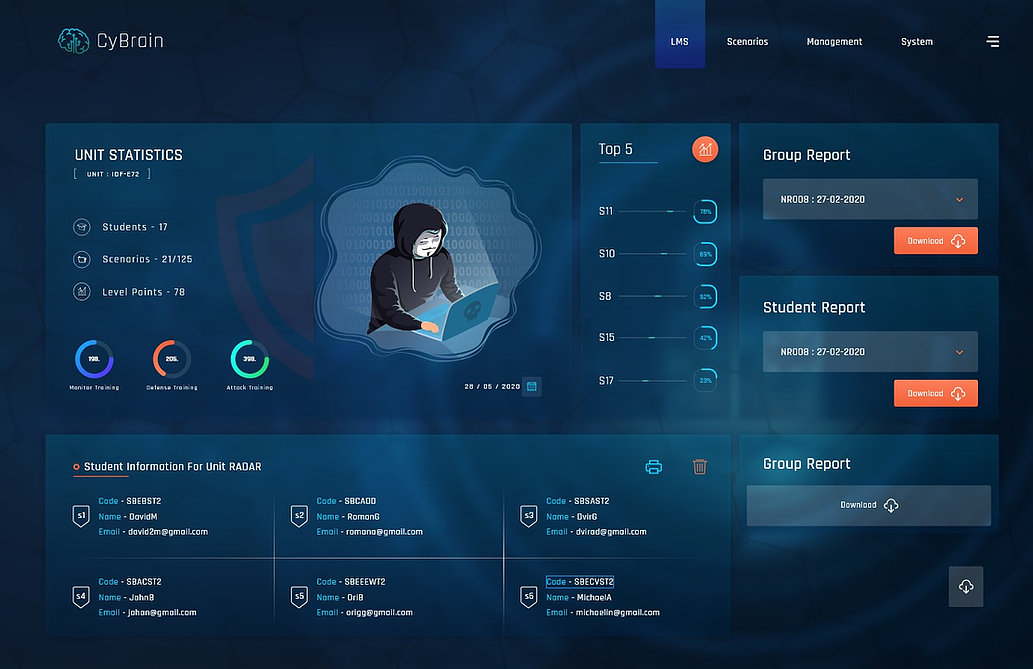
Cyberium LMS & Arena
The Cyberium Arena is a high-end cybersecurity Learning Management System and Simulator.