Threat Hunting
5 Days online

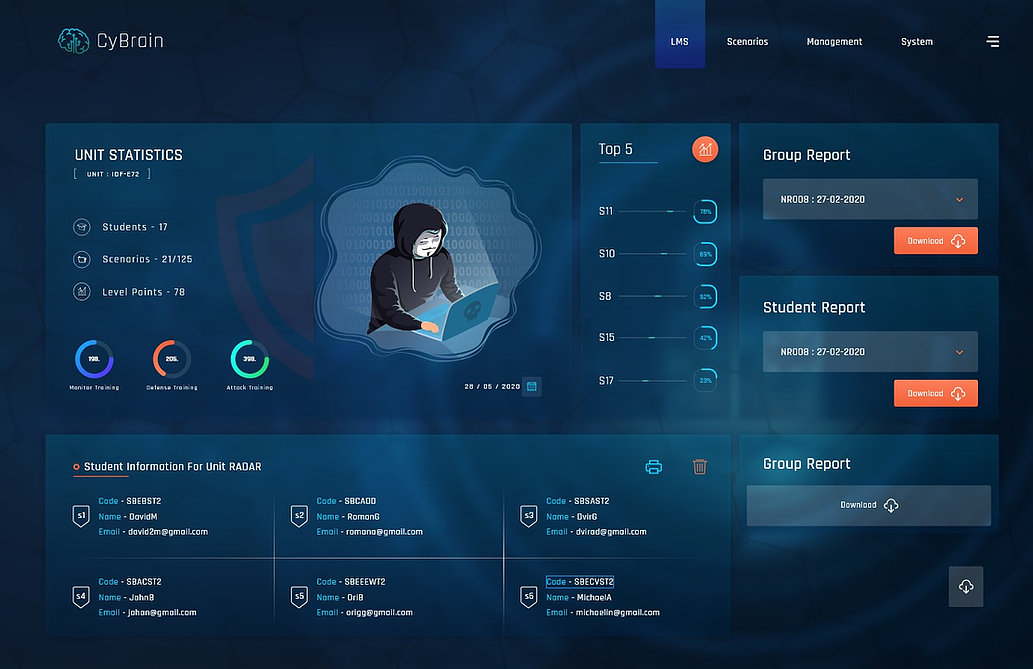
In today’s cybersecurity landscape, it isn’t possible to prevent every attack. Threat hunting is the proactive technique that focuses on pursuing attacks and the evidence that attackers leave behind when they perform an attack using malware or expose sensitive data.
The process is important and based on assuming that the attacker has already managed to infriltrate the system. The participant will learn to test everything possible to detect intrusion earlier to stop intruders before they can carry out their attacks and exploit them illegally.
This course is essential for:
Specialists and operatives with networking knowledge who want to acquire the threat hunting capabilities to protect their organization better.
- Network administrators/specialists
- Security Testers
- Cybersecurity consultants
- Red Team specialists
- White hat hackers
Cyberium Arena

Real Cases Studies
Remain informed about the training schedule:
More about:
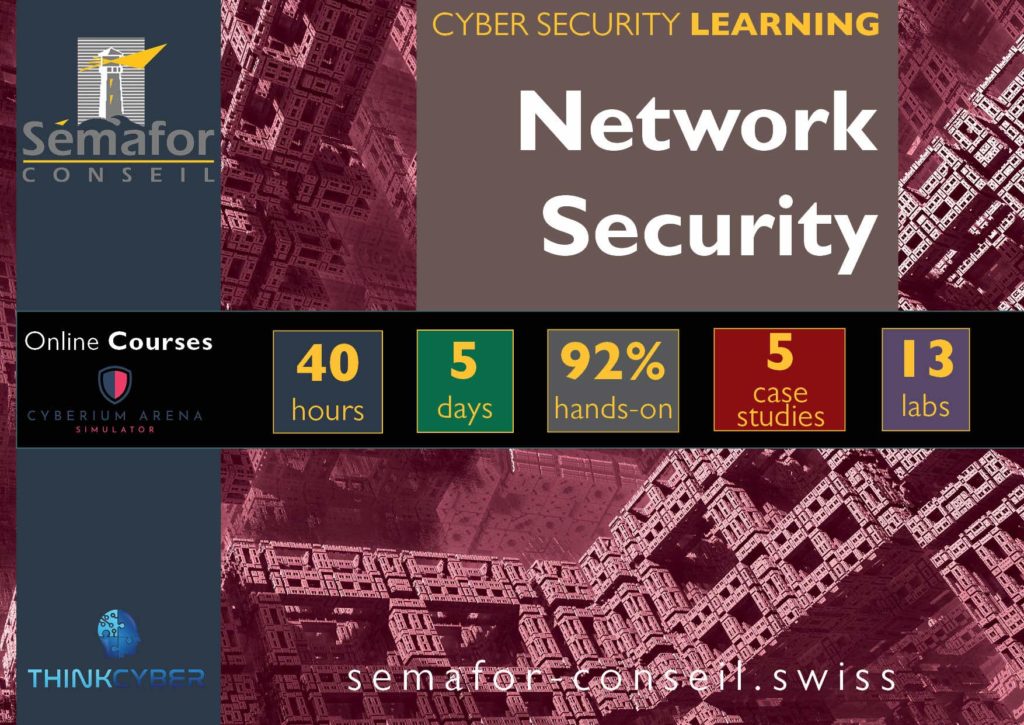
The Network Security course trains basic skills in the search for cyber threats.
The Intrusion Testing (PenTest) course provides additional skills in search and defense against attacks.