Cybersecurity Learning Process
Our Learning Management Approach
Semafor Conseil’s learning management is participant centric. The enrollment of the practitioner is carefully planned and articulated in order to provide him with the best possible learning experience.
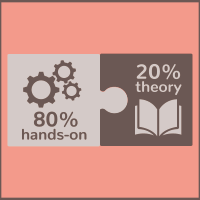
Once entered into the participant management process (personalized coaching), the practitioner will be invited to come and get involved in the chosen training, in our Cyberium Arena (LMS). The latter is a virtual learning and training zone, disconnected from any system, which will allow the practitioner to learn, test, train, all the tips and tricks related to his profession. Without danger, the practitioner will spend 80 to 90% of his training time in this Cyberium Arena. Whether it is for the simulations or for the labs, the examples taken by the facilitator are the most recent and always as close to reality as possible.
Of course, all this practice will be supported by the most robust theories (20% of the remaining time).
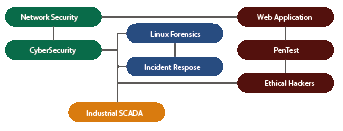
Our trainings are delivered in “sequential” mode (one day per week over 5 weeks). This mode enables the participants to have time to harness the content of the courses in a much deeper fashion than with a block approach. It also provides the participants the opportunity to build a meaningful project.
In addition, in order to provide maximum flexibility and comfort and to let the participant focus 100% on his training, it can be followed from the place of his choice (home office, office, nomad), in agreement with his employer.
One training day is one aquired skill
Flexible training mode
Learning from practice

Secured & dedicated LMS
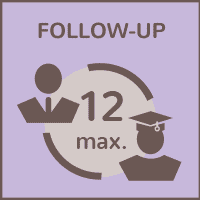
Limited to 12 participants, individual follow-up

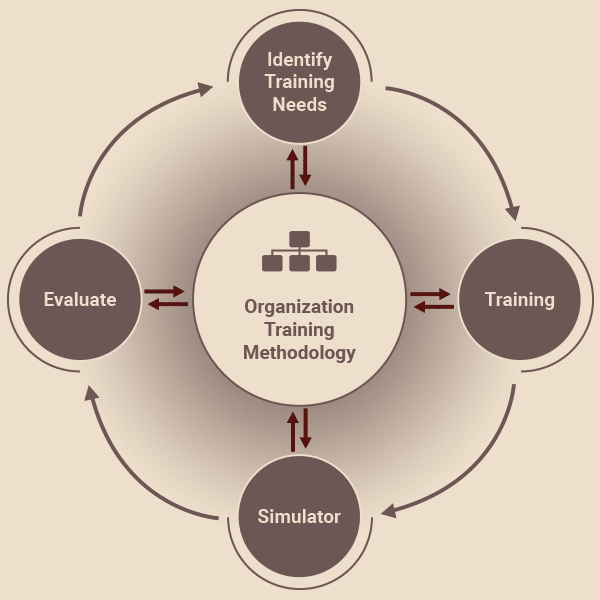
Check, Learn, Practice, Evaluate
Benefits for:
Human Resources
For Human Resources Managers, we create efficient training paths, which are palatable and enabling participants to keep their agendas available 4 days a week for the duration of the course, thus providing an immediate return on investment throughout the course, from the first training day, as the practitioners can incorporate its learnings into their daily practice.
IT & Cybersecurity Management
For managers, we offer training modules that provide the most current topical knowledge in cybersecurity in order for the participants to deliver an immediate return on investment with strong and engageable technical skills, which the practitioners can leverage with confidence on the job.
Practitioners
For the company’s practitioners, we create unique conditions for effective and innovative courses focused on cybersecurity, leveraging the most up-to-date training environment, where participants can explore and discover safely the uses of the tools they are exposed to. The practitioners are supported throughout the courses by a team of expert coaches and trainers, which will empower them to be successful; they can also leverage the acquired knowledge to pass related certifications.
Rethinking Cybersecurity Training?
Going Cyberium Arena!
Cybersecurity is not a teaching domain that can succeed without good practices:
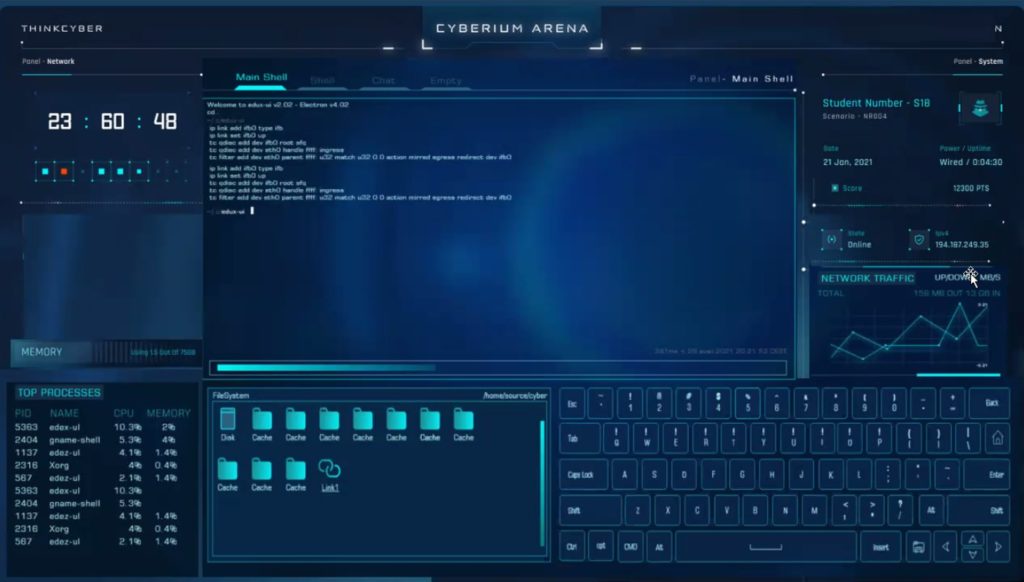
Today more than ever, the options for learning venues for cybersecurity are numerous. However only a handful offer real learning tools to support the knowledge acquisition process. ThinkCyber has developed a Learning Management System , which is dedicated to the teaching and training of Cybersecurity skills and competencies.
The Cyberium Arena incorporates:
- A comprehensive and mature Learning Management System providing tools for participants, including a comprehensive courseware covering classes, as well as labs, and case studies and their respective scenarios.
- An integrated virtual lab environment bridging the Information Technology and the Industrial Control Systems world therefor enabling the participants to work on complex case-studies seamlessly, while they can be supported pro-actively by live trainers and instructors.
- An efficient communication system for participants and instructor to communicate and exchange throughout the courses.
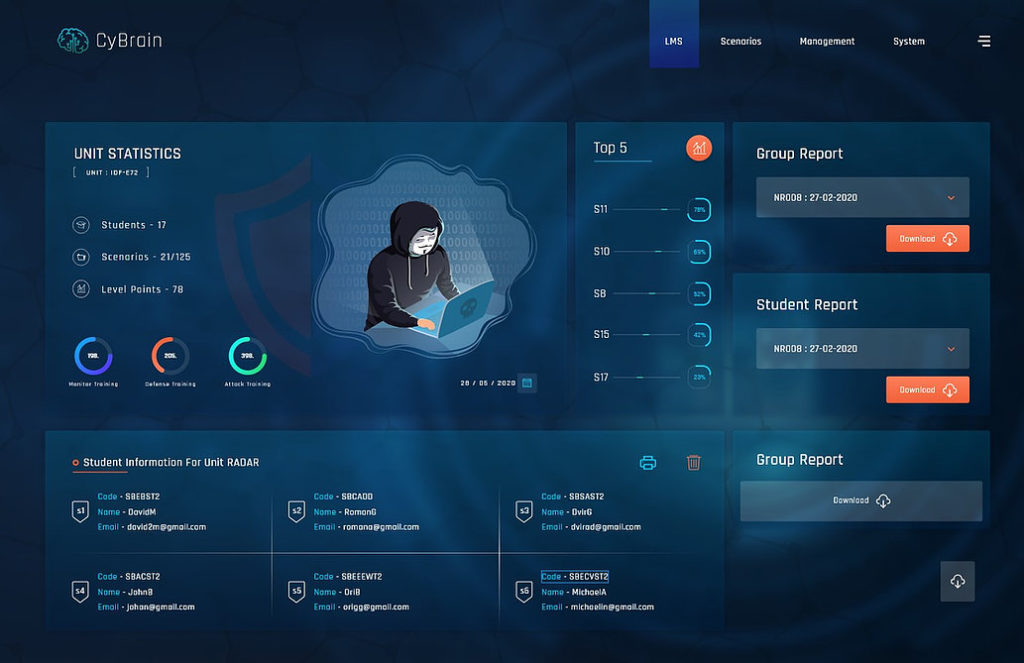
The Cyberium Arena enables the instructors to continuously monitor the progress of the participants and provide them support to enable them to gain the most from the courses.
The Cyberium Arena offers the opportunity for participants to work on real life scenarios which are reproduced in a safe and controlled environment, thus enabling the participants to stretch their limits without any security risk.
The Cyberium Arena is a virtual LMS solution offering a seamless learning experience to the course participants whatever the learning mode they chose: in situ, online or on-demand. Instructors, coaches and proctors are always available to address issues, questions, clarification requests, or even to provide hints to participants toward the solution when faced with a difficult lab or scenario.
CyberLearning - Educational Process
Cybersecurity is not a teaching domain that can succeed without good practices:
- Instructors receive dedicated training pertaining to the teaching methods, the courses and their syllabus.
- The educational content is developed and vetted by industry experts. The course material is reviewed very frequently, in order to keep up with the industry’s best practices and the evolution of the threat landscape.
- The Learning Environment is focused toward practicality and provides the participants with all the courseware and resources required to attend and make the most out of the course.
- The courses and the program management are managed through a continuous QA process, where feedback from the instructors and the participants is actively sought.
- The environmental alignment is maintained as our instructors are field practitioners who share their accrued experience with the participants.
Our training methodology follows a hands-on continuous improvement approach, whereby knowledge is continuously evaluated against practice, thereby identifying and addressing the additional training needs of the participant.
Using real Cases Studies
Courses open for subscription
Hands-on / Theory Mix
Our approach is to give the participants the opportunity to apply the studied knowledge directly with hands-on exercises and case studies; we aim for a high ratio, which hits an average over our complete course portfolio:
Labs & Cases studies
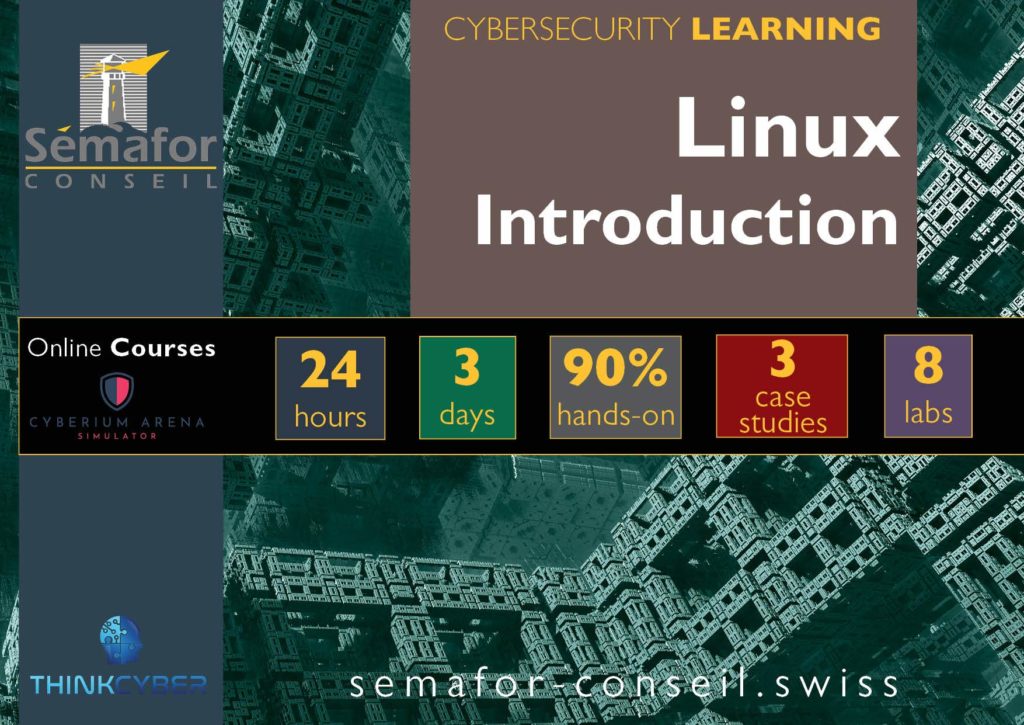
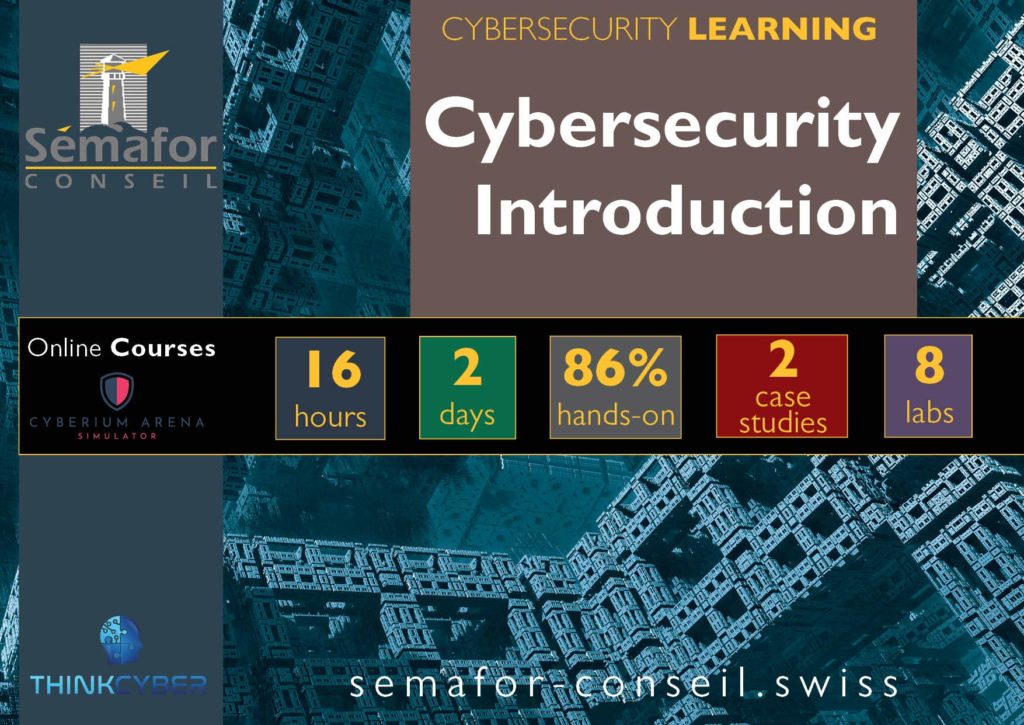
The course portfolio is incorportating a large number of labs and case studies:
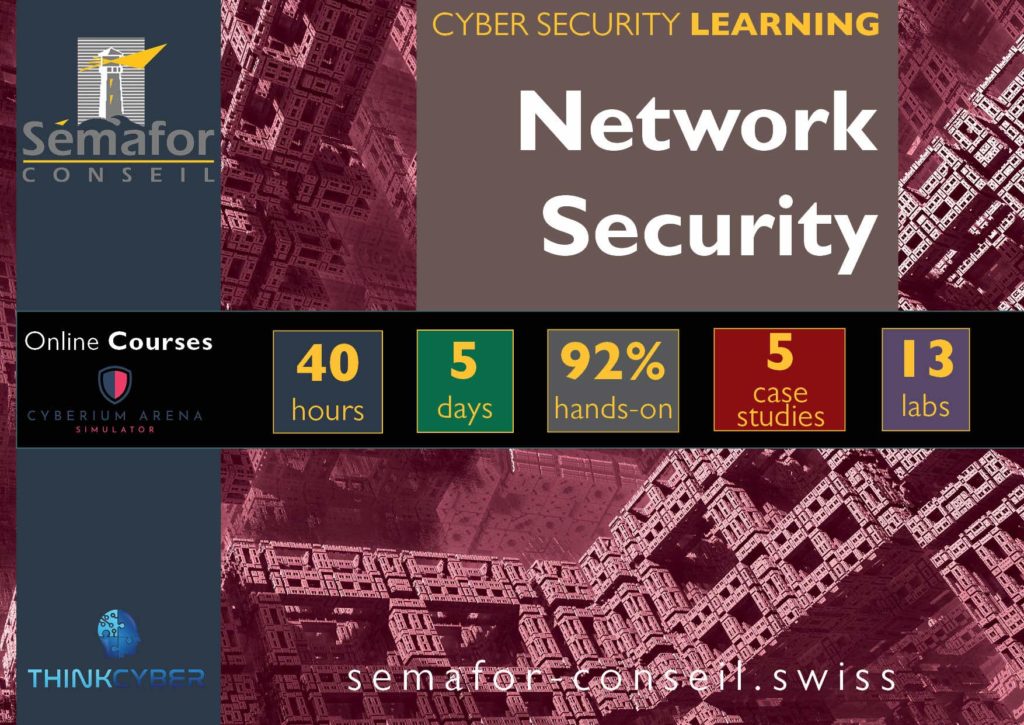
Cybersecurity Course Corpus
Our Cybersecurity courses corpus covers all of the core domain (PenTest, Monitoring, Incident Responses…) and technical domain (Web Security, Industrial Control Systems, Cyber Investigation…)