The usual situation
In organizations, there are computer networks, with computer systems, which run applications (web or other). There is also a whole bunch of people who have access to the network: employees, consultants, partners, family (eg: the boss who gives access to the network to his student nephew), suppliers, and others.
These people use a workstation, most often a corporate one, but sometimes it’s a personal computer, tablet, smartphone, etc. Everyone has access to the Internet from the corporate network, and can use any software they want, and interact with their favorite websites.
Here are the ingredients for the perfect storm.
But what is the problem?
The problem is that these people, with all the goodwill in the world, are sure to expose the organization to all kinds of risks. Here are some examples:
– The nephew who uses a VPN like Hola (Hola.org) to visit a website in another country. You should know that Hola is a community VPN. If the nephew can use the connection of millions of other users, those same millions of users can use the organization’s Internet connection. In general, it’s not a good idea to have unidentified strangers secretly present on the network.
– The employee who creates an account on Dropbox or other file sharing facilities in order to facilitate exchanges with a partner. The risk is that company-owned files will end up on public file-sharing facilities, with perhaps an insufficient level of protection. Let’s not forget that large public sites are sometimes hacked. This was the case for Dropbox again in July 2021 with the compromise of 68 million accounts. No one wants to be part of these accounts.
– The partner who establishes a VPN link with his employer to recover a software tool. If their employer’s network is infected with viruses, ransomware, or other annoyances, the organization’s network can in turn be infected. This type of network interconnection bypasses any protections the organization may have deployed at the network level.
– And countless variations on similar scenarios.
How to protect yourself from these risks?
The answer to this question may sound simplistic, but it’s the same as protecting your home.
In my house, I make sure that only the people I allow to have a key, have one. In general, I make sure that the inhabitants of the house know the behaviors that are not accepted: we do not make a bonfire in the house, we do not play with weapons, we do not fill a swimming pool in the living room, etc.
Rooms to which access is prohibited are locked. Surveillance cameras may be installed. There is a list of people that members of the household may invite. All other people are excluded, unless special permission is given.
Back on topic. The main principle of cybersecurity is that only authorized persons have access to resources to which access has been specifically granted to them. This access must be made via the only mechanisms allowed.
To this end, here is a series of measures to be deployed to achieve this result:
- Access to the network is controlled and authenticated (2 factor)
- Only corporate workstations are allowed. No personal device.
- No one is an administrator of their workstation. All installed software must be authorized and installed by IT support.
- Internet access is controlled and sites unrelated to company business are blocked. Some organizations will allow access to Gmail, or other to allow employees to view their personal email.
- Some protocols (such as VPNs) are blocked outbound.
- Devices for detecting malicious or risky activity are deployed.
These 6 little security measures will protect the organization from those inside (albeit unintentional) hackers that the people in and around the company are. Experts call these people “insiders”.
The vast majority of insiders who expose the company to cybersecurity risks do so by accident or ignorance. There is however a small portion of the insiders who aim for financial gain and are therefore malicious. It’s harder to defend against them, and we’ll cover that in another upcoming article.
The storm that becomes a hurricane
One trend that is emerging at the moment is for criminal organizations to recruit employees of the targeted company to deploy ransomware on corporate servers. The criminal organizations that are doing this recruiting are promising huge sums of money as payment, and promise that the perpetrator of this deployment will not be caught because the evidence will be encrypted by the ransomware.
The prospect of an employee who has privileged access to the entire network and who is trusted by the company, “offering” the corporate network to criminals, is frightening. Here we are at the point where we must be suspicious of employees, and even protect yourself from them. Throughout history there have been anecdotes of employees who have been perverted by criminals. The difference here is that the criminals are announcing it loud and clear.
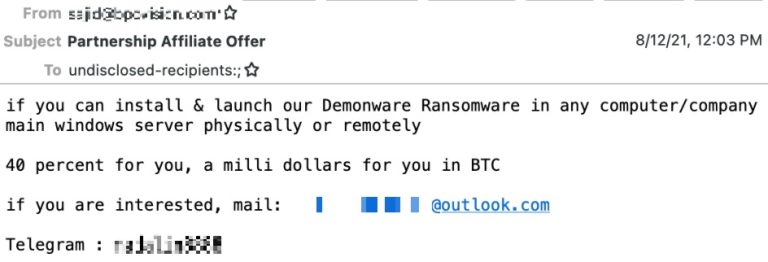
The 6 measures listed above can offer protection against these situations, provided that these measures are not administered by company personnel. Thus, without having access to them, an employee who converted to crime would not be able to deactivate them.
If necessary, Sémafor Conseil can help you implement these measures.